Unix for Busy People - Logging in, Secure Shell and the Network: Difference between revisions
| Line 112: | Line 112: | ||
$ ifconfig (need to be root on some cases) | $ ifconfig (need to be root on some cases) | ||
$ ping | $ ping | ||
Latest revision as of 23:57, 25 March 2021
While I don't want to get bogged down into too much detail in networking a certain amount of familiarity is needed when trying to troubleshoot problems and diagnose connection failures.
Network
A network allows other computers that are a member of that network or members of an inter-connected network (via routers or gateways) to communicate. Usually there are access rules that govern the ingress and egress to and from one computer network to another. The device that usually controls this access is called a firewall although sometime this can be accomplished with a router using an Access Control List or ACL for more broad access controls.
Reference: http://en.wikipedia.org/wiki/Computer_network
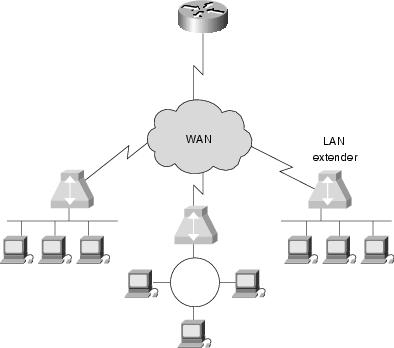
A computer network is a group of computers that are connected to each other for the purpose of communication. Any computer network is classified on the basis of a wide variety of characteristics. Typically these classifications include: Connection method (wired or wireless), Scale, scope and purpose (LAN, WAN or SAN) or Topology. For this class we will only talk about the first two.
Networks are often classified as Local Area Network (LAN), Wide Area Network (WAN), Metropolitan Area Network (MAN), Personal Area Network (PAN), Virtual Private Network (VPN), Campus Area Network (CAN), Storage Area Network (SAN), etc. depending on their scale, scope and purpose. Usage, trust levels and access rights often differ between these types of network - for example, LANs tend to be designed for internal use by an organization's internal systems and employees in individual physical locations (such as a building), while WANs may connect physically separate parts of an organization to each other and may include connections to third parties.
Connection methods
Connection methods are usually broken down by wired (Ethernet or modem) and wireless (Wi-Fi, satellite or cellular modem). Typically on a wired network your first connection layer is the physical network you are connected to. In the case of a wired connection this would be the LAN. A LAN is typically 8 pin jacks terminated in a hall closet some where that are terminated on what is called a switch. A switch can either be a standalone box but more typically in a corporate environment are actually a single blade or card inside a much larger chassis or enclosure. Switches allow a technology to be deployed referred to as a VLAN or virtual LAN.
The Seven-Layer model
Reference: http://en.wikipedia.org/wiki/OSI_model
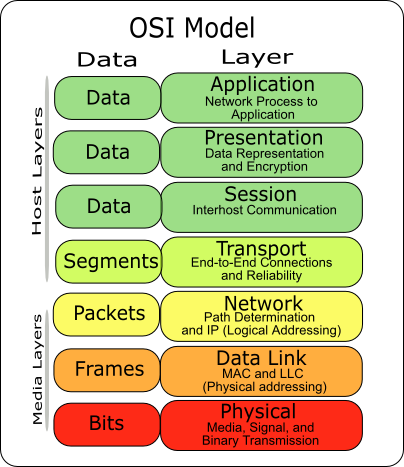
The International Organization for Standardization (ISO) developed the Open Systems Interconnection (OSI) Reference Model to describe how information is transferred from one machine to another, from the point when a user enters information using a keyboard and mouse to when that information is converted to electrical or light signals transferred along a piece of wire or radio waves transferred through the air. It is important to understand that the OSI Reference Model describes concepts and terms in a general manner, and that many network protocols, such as Internet Protocol (IP), fail to fit nicely into the scheme explained in ISO’s model.
Therefore, the OSI Reference Model is most often used as a teaching and troubleshooting tool. By understanding the basics of the OSI Reference Model, you can apply these to real protocols to gain a better understanding of them as well as to more easily troubleshoot problems.
ISO developed the seven-layer model to help vendors and network administrators gain a better understanding of how data is handled and transported between networking devices, as well as to provide a guideline for the implementation of new networking standards and technologies. To assist in this process, the OSI Reference Model breaks the network communication process into seven simple steps.
The Network Layers
Think of the seven layers as the assembly line in the computer. At each layer, certain things happen to the data that prepare it for the next layer. The seven layers, which separate into two sets, are:
Application Set:
- Layer 7: Application - This is the layer that actually interacts with the operating system or application whenever the user chooses to transfer files, read messages or perform other network-related activities.
- Layer 6: Presentation - Layer 6 takes the data provided by the Application layer and converts it into a standard format that the other layers can understand.
- Layer 5: Session - Layer 5 establishes, maintains and ends communication with the receiving device.
Transport Set:
- Layer 4: Transport - This layer maintains flow control of data and provides for error checking and recovery of data between the devices. Flow control means that the Transport layer looks to see if data is coming from more than one application and integrates each application's data into a single stream for the physical network.
- Layer 3: Network - The way that the data will be sent to the recipient device is determined in this layer. Logical protocols, routing and addressing are handled here.
- Layer 2: Data - In this layer, the appropriate physical protocol is assigned to the data. Also, the type of network and the packet sequencing is defined.
- Layer 1: Physical - This is the level of the actual hardware. It defines the physical characteristics of the network such as connections, voltage levels and timing.
Protocol Stacks
A protocol stack is a group of protocols that all work together to allow software or hardware to perform a function. The TCP/IP protocol stack is a good example. It uses four layers that map to the OSI model as follows:
- Layer 1: Network Interface - This layer combines the Physical and Data layers and routes the data between devices on the same network. It also manages the exchange of data between the network and other devices.
- Layer 2: Internet - This layer corresponds to the Network layer. The Internet Protocol (IP) uses the IP address, consisting of a Network Identifier and a Host Identifier, to determine the address of the device it is communicating with.
- Layer 3: Transport - Corresponding to the OSI Transport layer, this is the part of the protocol stack where the Transport Control Protocol (TCP) can be found. TCP works by asking another device on the network if it is willing to accept information from the local device.
- Layer 4: Application - Layer 4 combines the Session, Presentation and Application layers of the OSI model. Protocols for specific functions such as e-mail (Simple Mail Transfer Protocol, SMTP) and file transfer (File Transfer Protocol, FTP) reside at this level.
As you can see, it is not necessary to develop a separate layer for each and every function outlined in the OSI Reference Model. But developers are able to ensure that a certain level of compatibility is maintained by following the general guidelines provided by the model.
!!!Transmission:
Data is transmitted between computers and network devices via what is commonly referred to as a Network Interface Card or NIC. As a requirement of unique addressing each NIC has at least one Media Access Control or MAC address. The standard (IEEE 802) format for printing MAC-48 addresses in human-friendly form is six groups of two hexadecimal digits, separated by hyphens (-) or colons (:), in transmission order, e.g. 01-23-45-67-89-ab, 01:23:45:67:89:ab. The primary MAC is usually hardwired by the vendor and the first three digits bytes are actually pre-assigned to a particular vendor by the industry.
Reference: http://en.wikipedia.org/wiki/MAC_address
TCP/IP
Transmission Control Protocol/Internet Protocol or The Internet Protocol Suite (commonly known as TCP/IP) has been standard protocol stack for inter-networked communications for the last 15 years has been TCP/IP. It is this way at HMH. TCP/IP requires the first five layers of network communication. TCP is a stateful reliable albeit chatty protocol. However some transmission do not require acknowledgment or guaranteed delivery hence reducing traffic. For those applications there also exists another protocol that is sometimes used over IP called User Datagram Protocol or UDP. Particularly Unix services commonly referred to as Remote Procedure Call or RPC typically use UDP which is stateless. Lacking reliability, UDP applications must generally be willing to accept some loss, errors or duplication. Some applications such as TFTP may add rudimentary reliability mechanisms into the application layer as needed. Most often, UDP applications do not require reliability mechanisms and may even be hindered by them. Streaming media, real-time multiplayer games and voice over IP (VoIP) are examples of applications that often use UDP. If an application requires a high degree of reliability, a protocol such as the TCP would be used instead. All IP, UDP and TCP operate in the Transport Layer of the Seven-Layer model.
Unix network
The Transport Layer requires three things to make a successful transmission: an established Link Layer (hardware) a IP address and a source and destination port.
On a Unix system certain services are usually listening to a particular port number on one or more particular IP addresses. This is referred to as being bound. In order to be useful a Unix system has one or more external addresses known to the locally connected network. Sometimes there are multiple networks connected the Unix computer for different purposes such as for backups to reduce traffic on the primary interface or network. However all Unix systems also have a standard internet network as well called the loopback address. This address is always 127.0.0.1 and cannot be used externally. The loopback address allows Unix processes on the same server to communicate with each other. Service processes (referred to as daemons) sometimes are listening to loopback only for security reasons such as a web server listening externally but using a database application that is only accessible via the loopback address. IP address are noted in human readable form as four octets and sometimes with subnetwork bits(known as Classless Inter-Domain Routing (CIDR) notation) separated by dots such as 192.168.1.5. Each octet designates a subnetwork class in the routing topology for a given network. All of this must be designed in advance with careful planning. So you should thank your Network Engineers they made all of this happen. Some IP address are not meant to route onto the public Internet and as such some IP address classes (10.*.*.* or 192.168.*.* for example) are used for this purpose inside company networks which stand behind an Internet gateway using Network Address Translation or NAT. For this reason publicly registered addresses are scarce and also expensive.
Reference: http://en.wikipedia.org/wiki/IP_address
Devices
On Unix-like systems, the loopback interface usually has the device name lo or lo0. On Solaris NIC's have various chip-set names such as bge, hme or le and end with a sequence number such as hme0 or bge23. In Linux Ethernet devices start with eth and like Solaris end with a sequence number like eth0 or eth5.
Trivia the actual name for the hme device in Solaris is called "Happy Meal Ethernet". bge is the Broadcom Gigabit Ethernet adapter and le (seldom seen any more) stands for Lance Ethernet the first type delivered and is only capable of 10mb/sec.
Sockets
Network communication between processes and devices on Unix systems is accomplished via sockets which is pockets of memory set aside for this purpose and require device drivers in order to deliver the data to a particular piece of hardware.
Name services
Since you must know a remote systems IP address in order to communicate with it it is easier to use DNS or Domain Name Services to refer to it by name. Names like hmhpub.com or rofl.fred.com are much easier to remember. DNS services are usually provided by your Internet Service Provider or ISP upstream. Here at HMH we have a number of dedicated servers for this purpose and Unix systems here are configured to use those services. However know that if the DNS services fail (or you have connectivity problems) connections may not work properly or at all until the service is restored.
Unix services
Unix services are run by processes referred to as daemons and are either started at boot-time or they make be invoked from the Internet Service Daemon known as inetd. To be started from inetd their port number must be registered with the system usually in /etc/system file.
Secure Shell
Secure Shell or SSH is a network protocol that allows data to be exchanged using a secure channel between two networked devices. Used primarily on Unix based systems to access shell accounts, SSH was designed as a replacement for Telnet and other insecure remote shells, which send information, notably passwords, in plaintext, leaving them open for interception. The encryption used by SSH provides confidentiality and integrity of data over an insecure network, such as the Internet. SSH is the standard way of logging into a remote Unix system at HMH.
See also Using Secure Shell.
Unix network commands to know
$ netstat
$ ifconfig (need to be root on some cases)
$ ping
$ traceroute (need to be root on some cases)
More information
Topics like subnet-masking and network routes are really beyond the scope of this class however for more information I refer you to the book TCP/IP Network Administration, Third Edition.